Privilige Escalation
Privilege Escalation
This time I will discuss about privilege escalation.
Here I will look for login username on debian linux that I use in vitualbox
The first look for information that is on debian gathering is here I use nmap and I use it for Nessus vulnerability and exploit db.
the second. entered on exploit.db and started looking for anything that is running the service on debian linux
from the above picture there is a name obama, osama and obama. and besides these names exist alloy numbers and letters. it is the password of the username. but the password is still encrypted.
and to know the actual password we use john the ripper to crack the password
but before using john the ripper.copy first results of the perl files we have open through exploit.db earlier. and make a txt file and then save the file john the ripper
Here I give a name that has become a txt file before the name uye.txt.lalu enter and wait. fairly long time. should be patient and allow the coffee to avoid drowsiness. ^ _ ^
This time I will discuss about privilege escalation.
Here I will look for login username on debian linux that I use in vitualbox
The first look for information that is on debian gathering is here I use nmap and I use it for Nessus vulnerability and exploit db.
the second. entered on exploit.db and started looking for anything that is running the service on debian linux
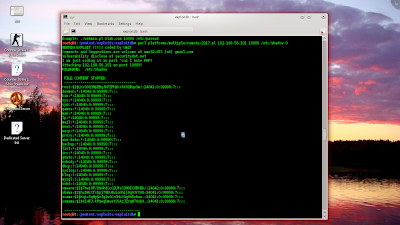
here I use webmin. because of the image of the first. use an open port on port 10000 services running http (webmin).
the third. I began to open the files that I have selected from the above picture contained from webmin using perl command platforms/multiple/remote/2017.pl 192.168.56.101 10000. and look going out there to know his username. by typing in the terminal / etc / passwd 0
but I would not use / etc / passwd 0 but I would use / etc.shadow 0 in order to know his password too
and to know the actual password we use john the ripper to crack the password
but before using john the ripper.copy first results of the perl files we have open through exploit.db earlier. and make a txt file and then save the file john the ripper
Here I give a name that has become a txt file before the name uye.txt.lalu enter and wait. fairly long time. should be patient and allow the coffee to avoid drowsiness. ^ _ ^
A few explanations Privilege Escalation of me. may be useful





0 comments:
Post a Comment