Buffer Overflow winamp crash
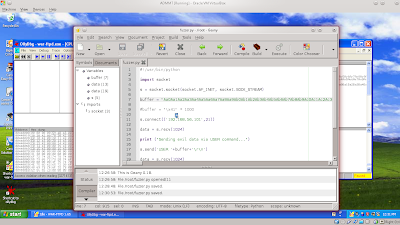
The first makes fuzzer to send garbage data.
Here I make the data in the form of a character as much as 30 000
help click and select about who is on winamp
alhamdulillah its successful EIP and ESP crushed
for its onwards I will continue later. so thank you. regards uyee
Here I make the data in the form of a character as much as 30 000
then run the python file that you have created with the command
root @ bt :/ var / www / uye # python ijoagomo.py. I save this file in the root directory / var / www with the file name ijoagomo.py
root @ bt :/ var / www / uye # python ijoagomo.py. I save this file in the root directory / var / www with the file name ijoagomo.py
after run python file earlier. let go of existing windows and download the results generat divirtualbox python file into whatsnew.txt
before downloading the file. apache start there first dibacktrack
before downloading the file. apache start there first dibacktrack
once downloaded. save the file and move it into program files and copy kefolder winamp
after his whatsnew.txt file copy application run winamp with OllyDbg. and select the help menu and select about and see what happens in the memory registers. EIP and ESP it will overwrite and will cause the character "aaaaaaaa"
help click and select about who is on winamp
alhamdulillah its successful EIP and ESP crushed
for its onwards I will continue later. so thank you. regards uyee